
Companies and public authorities rely on databases to store and process large amounts of data. These databases typically manage business-critical and highly sensitive information, such as financial data (tax records, bank accounts, and credit cards), personal data (home addresses and personnel files), or product data. Since the databases are usually integrated with applications and web services, they remain vulnerable to cyberthreats both internally and externally.
Many CIOs and IT leaders believe that their IT infrastructure is adequately protected against cyberattacks. Multi-level firewalls, antivirus software, and intrusion detection and prevention systems (IPS)(1) provide a false sense of security. What many fail to recognize is that the biggest security risk often comes from within—the employees and officials using these systems.
Employees and officials frequently fall prey to phishing emails or deceptive external callers, unwittingly clicking on malicious links or sharing confidential information with outsiders. This is often due to the fact that phishing emails and callers are no longer recognized as a threat. With the advancement of AI-driven deception, it is increasingly difficult to
identify threats. Stress and time pressure can lead to lapses in judgement, making employees more likely to make costly mistakes.
As a result, cyberattacks continue to succeed. In a recent study by the European Cybersecurity Agency (ENISA)(2) security experts found that companies and authorities in the European Union, in particular, have become the target of cyberattacks in the last 12 months.
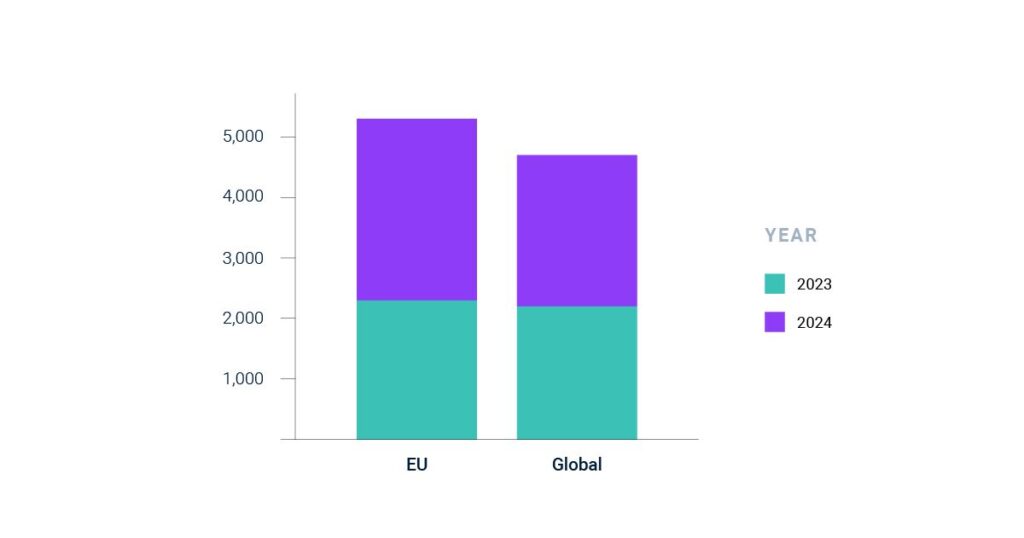
Number of incidents – EU and global (July 2023 – June 2024)
An analysis of individual sectors reveals that the public sector is particularly hard hit, accounting for 19% of attacks, followed by the transport sector (11%) and banking and finance (9%). This is not surprising—many still remember the high-profile cyberattacks targeting the German Bundestag, municipalities, university hospitals, Dutch law enforcement, and Spanish citizens and authorities.(3-8)
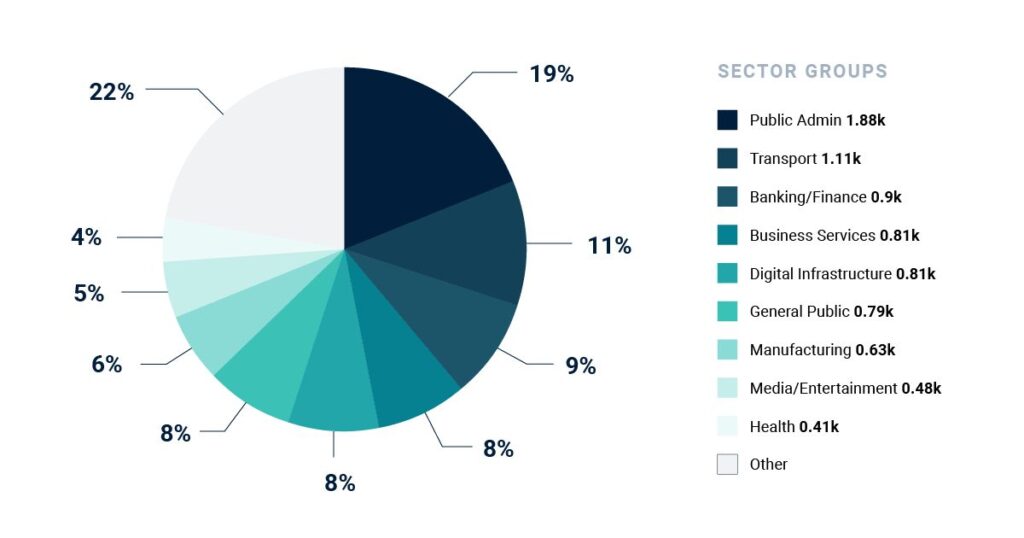
Affected sectors – The public sector is the most affected! (July 2023 – June 2024)
Breaking down cyber threats by category, the direct threat to stored data—primarily databases—is 45% with 19% of incidents involving data breaches and 26% of incidents involving ransomware attacks (2).
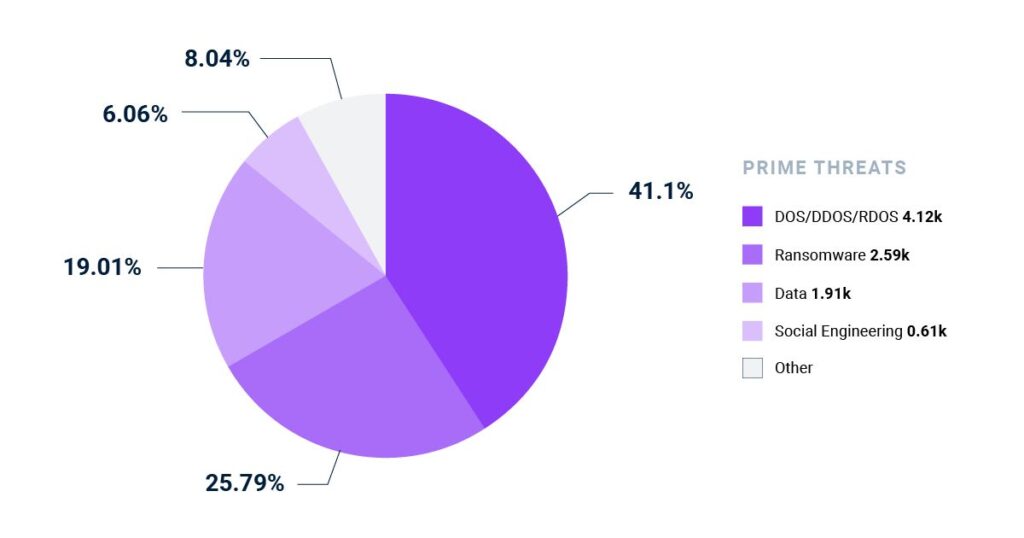
Analysis of threats by type
Under Article 32 of the GDPR(9) (Security of Processing) the following is required: “…the controller and the processor shall implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk.”
Specifically it highlights, “the pseudonymization and encryption of personal data“as an effective measure.
Additionally, the German Federal Office for Information Security (BSI) also recommends encryption as a key strategy to minimize the risk of IT operations in its BSI Standards(10) 200-1 to 200-4.
Under Article 33 of the GDPR(9) (Notification of a personal data breach to the supervisory authority), companies are required to notify a personal data breach to the supervisory authority within 72 hours of becoming aware of the breach. The data controller must notify the relevant supervisory authority in accordance with Article 55 unless the break is unlikely to risk individuals’ rights. If the notification is delayed beyond 72 hours, an explanation for the delay must be provided.
Despite the clear guidelines, uncertainty remains in the IT world regarding the correct application of GDPR reporting requirements.
To clarify this, the European Data Protection Board (EDPB) has developed guidelines(11), including case studies.
In “CASE No. 01: Ransomware with proper backup and without exfiltration,” the following scenario is described:
“Computer systems of a small manufacturing company were exposed to a ransomware attack, and data stored in those systems were encrypted. The data controller used encryption at rest, so all data accessed by the ransomware was stored in encrypted form using a state-of-the-art encryption algorithm. The decryption key was not compromised in the attack, i.e. the attacker could neither access it nor use it indirectly. In consequence, the attacker only had access to encrypted personal data.”
The necessary measures are set out in the table published in the guidelines:

The necessary measures are justified as follows:
“In this example, the attacker had access to personal data and the confidentiality of cipher text containing personal data in encrypted form was compromised. However, any data that might have been exfiltrated cannot be read or used by the perpetrator, at least for the time being. The encryption technique used by the data controller conforms to the state-of-the-art. The decryption key was not compromised and presumably could also not be determined by other means. In consequence, the confidentiality risks to the rights and freedoms of natural persons are reduced to a minimum barring cryptanalytic progress that renders the encrypted data intelligible in the future.”
Because of this, the company was not required to report the incident to authorities or affected individuals.
When comparing the cost of implementing IT security measures with the potential loss of reputation, sales, and customer trust, the benefits of proactive invetment quickly becomes clear.
In today’s hyperconnected world, where news spreads instantly through online platforms and social media, organizations must not underestimate the long-term damage caused by a cyberattack.
To mitigate risks, Software AG strongly recommends that its customers implement encryption(12) and auditing(12) for our Adabas databases to keep IT risks at a minimum. Both measures complement each other and form the optimal technology mix to protect against attacks and unwanted internal and external data leaks.
(1) https://www.gartner.com/reviews/market/intrusion-prevention-systems
(2) https://www.enisa.europa.eu/publications/enisa-threat-landscape-2024
(3) https://www.auswaertiges-amt.de/en/newsroom/news/hacker-attack-bundestag-2345580
(4) https://www.dw.com/en/germany-cybercrime-by-foreign-actors-rose-by-28-in-2023/a-69065980
(5) https://www.heise.de/en/news/After-cyber-attack-Suedwestfalen-IT-wants-to-reform-itself-profoundly-10188167.html
(6) https://www.bbc.com/news/technology-54204356
(7) https://www.dutchnews.nl/2024/09/police-leak-leaves-data-of-62000-officers-in-hands-of-hackers/
(8) https://www.statista.com/topics/7011/cyber-crime-in-spain/#topicOverview
(9) https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32016R0679
(10) https://www.bsi.bund.de/EN/Themen/Unternehmen-und-Organisationen/Standards-und-Zertifizierung/IT-Grundschutz/it-grundschutz_node.html
(11) https://www.edpb.europa.eu/our-work-tools/our-documents/guidelines/guidelines-012021-examples-regarding-personal-data-breach_en
(12) https://www.softwareag.com/app/uploads/2025/08/ebook-adabas-maximize-security-en.pdf.sagdownload.inline.1669044425901.pdf